The Worldwide Computer
An operating system spanning the Internet would bring the power of millions of the world's Internet-connected PCs to everyone's fingertipsSUBTOPICS
SIDEBARS
Existing Distributed Systems
Primes and Crimes
ADDITIONAL RESOURCES
RELATED LINKS
 |
| PHILIP HOWE |
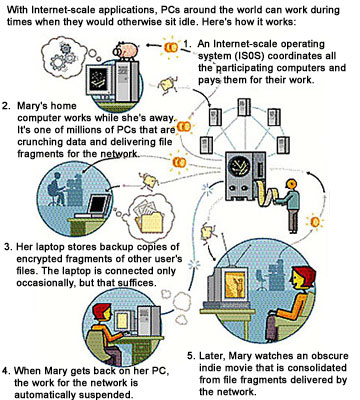
This sharing of resources doesn't stop at her desktop computer. The laptop computer in her satchel is turned off, but its disk is filled with bits and pieces of other people's files, as part of a distributed backup system. Mary's critical files are backed up in the same way, saved on dozens of disks around the world.
Later, Mary watches an independent film on her Internet-connected digital television, using a pay-per-view system. The movie is assembled on the fly from fragments on several hundred computers belonging to people like her.
Mary's computers are moonlighting for other people. But they're not giving anything away for free. As her PC works, pennies trickle into her virtual bank account. The payments come from the biotech company, the movie system and the backup service. Instead of buying expensive "server farms," these companies are renting time and space, not just on Mary's two computers but on millions of others as well. It's a win-win situation. The companies save money on hardware, which enables, for instance, the movie-viewing service to offer obscure movies. Mary earns a little cash, her files are backed up, and she gets to watch an indie film. All this could happen with an Internet-scale operating system (ISOS) to provide the necessary "glue" to link the processing and storage capabilities of millions of independent computers.
Internet-Scale Applications
Although Mary's
world is fictional--and an Internet-scale operating system does not yet
exist--developers have already produced a number of Internet-scale, or
peer-to-peer, applications that attempt to tap the vast array of
underutilized machines available through the Internet [see
box]. These applications accomplish goals that would be difficult,
unaffordable or impossible to attain using dedicated computers. Further,
today's systems are just the beginning: we can easily conceive of archival
services that could be relied on for hundreds of years and intelligent
search engines for tomorrow's Semantic Web [see "The
Semantic Web," by Tim Berners-Lee, James Hendler and Ora Lassila;
Scientific American, May 2001]. Unfortunately, the creation of
Internet-scale applications remains an imposing challenge. Developers must
build each new application from the ground up, with much effort spent on
technical matters, such as maintaining a database of users, that have
little to do with the application itself. If Internet-scale applications
are to become mainstream, these infrastructure issues must be dealt with
once and for all.
We can gain inspiration for eliminating this duplicate effort from operating systems such as Unix and Microsoft Windows. An operating system provides a virtual computing environment in which programs operate as if they were in sole possession of the computer. It shields programmers from the painful details of memory and disk allocation, communication protocols, scheduling of myriad processes, and interfaces to devices for data input and output. An operating system greatly simplifies the development of new computer programs. Similarly, an Internet-scale operating system would simplify the development of new distributed applications.
| MOONLIGHTING COMPUTERS |
 |
| XPLANE |
Two broad types of applications might benefit from an ISOS. The first is distributed data processing, such as physical simulations, radio signal analysis, genetic analysis, computer graphics rendering and financial modeling. The second is distributed online services, such as file storage systems, databases, hosting of Web sites, streaming media (such as online video) and advanced Web search engines.
What's Mine Is Yours
Computing today operates
predominantly as a private resource; organizations and individuals own the
systems that they use. An ISOS would facilitate a new paradigm in which it
would be routine to make use of resources all across the Internet. The
resource pool--hosts able to compute or store data and networks able to
transfer data between hosts--would still be individually owned, but they
could work for anyone. Hosts would include desktops, laptops, server
computers, network-attached storage devices and maybe handheld
devices.
The Internet resource pool differs from private resource pools in several important ways. More than 150 million hosts are connected to the Internet, and the number is growing exponentially. Consequently, an ISOS could provide a virtual computer with potentially 150 million times the processing speed and storage capacity of a typical single computer. Even when this virtual computer is divided up among many users, and after one allows for the overhead of running the network, the result is a bigger, faster and cheaper computer than the users could own privately. Continual upgrading of the resource pool's hardware causes the total speed and capacity of this über-computer to increase even faster than the number of connected hosts. Also, the pool is self-maintaining: when a computer breaks down, its owner eventually fixes or replaces it.
|
|
| More than 150 MILLION hosts are connected to the Internet, and the number is GROWING exponentially. |
|
|
In this way, the Internet-resource paradigm can increase the bounds of what is possible (such as higher speeds or larger data sets) for some applications, whereas for others it can lower the cost. For certain applications it may do neither--it's a paradigm, not a panacea. And designing an ISOS also presents a number of obstacles.
Some characteristics of the resource pool create difficulties that an ISOS must deal with. The resource pool is heterogeneous: Hosts have different processor types and operating systems. They have varying amounts of memory and disk space and a wide range of Internet connection speeds. Some hosts are behind firewalls or other similar layers of software that prohibit or hinder incoming connections. Many hosts in the pool are available only sporadically; desktop PCs are turned off at night, and laptops and systems using modems are frequently not connected. Hosts disappear unpredictably--sometimes permanently--and new hosts appear.
The ISOS must also take care not to antagonize the owners of hosts. It must have a minimal impact on the non-ISOS uses of the hosts, and it must respect limitations that owners may impose, such as allowing a host to be used only at night or only for specific types of applications. Yet the ISOS cannot trust every host to play by the rules in return for its own good behavior. Owners can inspect and modify the activities of their hosts. Curious and malicious users may attempt to disrupt, cheat or spoof the system. All these problems have a major influence on the design of an ISOS.
Who Gets What?
An internet-scale operating
system must address two fundamental issues--how to allocate resources and
how to compensate resource suppliers. A model based on economic principles
in which suppliers lease resources to consumers can deal with both issues
at once. In the 1980s researchers at Xerox PARC proposed and analyzed
economic approaches to apportioning computer resources. More recently,
Mojo Nation developed a file-sharing system in which users are paid in a
virtual currency ("mojo") for use of their resources and they in turn must
pay mojo to use the system. Such economic models encourage owners to allow
their resources to be used by other organizations, and theory shows that
they lead to optimal allocation of resources.
Even with 150 million hosts at its disposal, the ISOS will be dealing in "scarce" resources, because some tasks will request and be capable of using essentially unlimited resources. As it constantly decides where to run data-processing jobs and how to allocate storage space, the ISOS must try to perform tasks as cheaply as possible. It must also be fair, not allowing one task to run efficiently at the expense of another. Making these criteria precise--and devising scheduling algorithms to achieve them, even approximately--are areas of active research. The economic system for a shared network must define the basic units of a resource, such as the use of a megabyte of disk space for a day, and assign values that take into account properties such as the rate, or bandwidth, at which the storage can be accessed and how frequently it is available to the network. The system must also define how resources are bought and sold (whether they are paid for in advance, for instance) and how prices are determined (by auction or by a price-setting middleman).
Within this framework, the ISOS must accurately and securely keep track of resource usage. The ISOS would have an internal bank with accounts for suppliers and consumers that it must credit or debit according to resource usage. Participants can convert between ISOS currency and real money. The ISOS must also ensure that any guarantees of resource availability can be met: Mary doesn't want her movie to grind to a halt partway through. The economic system lets resource suppliers control how their resources are used. For example, a PC owner might specify that her computer's processor can't be used between 9 A.M. and 5 P.M. unless a very high price is paid.
Money, of course, encourages fraud, and ISOS participants have many ways to try to defraud one another. For instance, resource sellers, by modifying or fooling the ISOS agent program running on their computer, may return fictitious results without doing any computation. Researchers have explored statistical methods for detecting malicious or malfunctioning hosts. A recent idea for preventing unearned computation credit is to ensure that each work unit has a number of intermediate results that the server can quickly check and that can be obtained only by performing the entire computation. Other approaches are needed to prevent fraud in data storage and service provision.
The cost of ISOS resources to end users will converge to a fraction of the cost of owning the hardware. Ideally, this fraction will be large enough to encourage owners to participate and small enough to make many Internet-scale applications economically feasible. A typical PC owner might see the system as a barter economy in which he gets free services, such as file backup and Web hosting, in exchange for the use of his otherwise idle processor time and disk space.
A Basic Architecture
We advocate two basic
principles in our ISOS design: a minimal core operating system and control
by central servers. A computer operating system that provides only core
functions is called a microkernel. Higher-level functions are built on top
of it as user programs, allowing them to be debugged and replaced more
easily. This approach was pioneered in academic research systems and has
influenced some commercial systems, such as Windows NT. Most well-known
operating systems, however, are not microkernels.
The core facilities of an ISOS include resource allocation (long-term assignment of hosts' processing power and storage), scheduling (putting jobs into queues, both across the system and within individual hosts), accounting of resource usage, and the basic mechanisms for distributing and executing application programs. The ISOS should not duplicate features of local operating systems running on hosts.
|
|
| Curious and malicious USERS may attempt to DISRUPT, CHEAT or spoof the system. |
|
|
The ISOS server complex would maintain databases of resource descriptions, usage policies and task descriptions. The resource descriptions include, for example, the host's operating system, processor type and speed, total and free disk space, memory space, performance statistics of its network connections, and statistical descriptions of when it is powered on and connected to the network. Usage policies spell out the rules an owner has dictated for using her resources. Task descriptions include the resources assigned to an online service and the queued jobs of a data-processing task.
To make their computers available to the network, resource sellers contact the server complex (for instance, through a Web site) to download and install an ISOS agent program, to link resources to their ISOS account, and so on. The ISOS agent manages the host's resource usage. Periodically it obtains from the ISOS server complex a list of tasks to perform.
Resource buyers send the servers task requests and application agent programs (to be run on hosts). An online service provider can ask the ISOS for a set of hosts on which to run, specifying its resource requirements (for example, a distributed backup service could use sporadically connected resource hosts--Mary's laptop--which would cost less than constantly connected hosts). The ISOS supplies the service with addresses and descriptions of the granted hosts and allows the application agent program to communicate directly between hosts on which it is running. The service can request new hosts when some become unavailable. The ISOS does not dictate how clients make use of an online service, how the service responds or how clients are charged by the service (unlike the ISOS-controlled payments flowing from resource users to host owners).
An Application Toolkit
In principle, the
basic facilities of the ISOS--resource allocation, scheduling and
communication--are sufficient to construct a wide variety of applications.
Most applications, however, will have important subcomponents in common.
It is useful, therefore, to have a software toolkit to further assist
programmers in building new applications. Code for these facilities will
be incorporated into applications on resource hosts. Examples of these
facilities include:
- Location independent routing. Applications running with the ISOS can
spread copies of information and instances of computation among millions
of resource hosts. They have to be able to access them again. To
facilitate this, applications name objects under their purview with
Globally Unique Identifiers (GUIDs). These names enable "location
independent routing," which is the ability to send queries to objects
without knowing their location. A simplistic approach to location
independent routing could involve a database of GUIDs on a single
machine, but that system is not amenable to handling queries from
millions of hosts. Instead the ISOS toolkit distributes the database of
GUIDs among resource hosts. This kind of distributed system is being
explored in research projects such as the OceanStore persistent data
storage project at the University of California at
Berkeley.
Persistent data storage. Information stored by the ISOS must be able to survive a variety of mishaps. The persistent data facility aids in this task with mechanisms for encoding, reconstructing and repairing data. For maximum survivability, data are encoded with an "m-of-n" code. An m-of-n code is similar in principle to a hologram, from which a small piece suffices for reconstructing the whole image. The encoding spreads information over n fragments (on n resource hosts), any m of which are sufficient to reconstruct the data. For instance, the facility might encode a document into 64 fragments, any 16 of which suffice to reconstruct it. Continuous repair is also important. As fragments fail, the repair facility would regenerate them. If properly constructed, a persistent data facility could preserve information for hundreds of years.
Secure update. New problems arise when applications need to update stored information. For example, all copies of the information must be updated, and the object's GUID must point to its latest copy. An access control mechanism must prevent unauthorized persons from updating information. The secure update facility relies on Byzantine agreement protocols, in which a set of resource hosts come to a correct decision, even if a third of them are trying to lead the process astray.
Other facilities. The toolkit also assists by providing additional facilities, such as format conversion (to handle the heterogeneous nature of hosts) and synchronization libraries (to aid in cooperation among hosts).
An isos suffers from a familiar catch-22 that slows the adoption of many new technologies: Until a wide user base exists, only a limited set of applications will be feasible on the ISOS. Conversely, as long as the applications are few, the user base will remain small. But if a critical mass can be achieved by convincing enough developers and users of the intrinsic usefulness of an ISOS, the system should grow rapidly.
Further Information:
The Ecology of Computation. B. A. Huberman. North-Holland, 1988.
The
Grid: Blueprint for a New Computing Infrastructure. Edited by Ian Foster
and Carl Kesselman. Morgan Kaufmann Publishers, 1998.
Peer-to-Peer:
Harnessing the Power of Disruptive Technologies. Edited by Andy Oram.
O'Reilly & Associates, 2001.
Related Links:
Many research projects are working toward an
Internet-scale operating system, including:
Chord: www.pdos.lcs.mit.edu/chord/
Cosm: www.mithral.com/projects/cosm/
Eurogrid: www.eurogrid.org/
Farsite: http://research.microsoft.com/sn/farsite/
Grid Physics
Network (Griphyn): www.griphyn.org/
OceanStore: http://oceanstore.cs.berkeley.edu/
Particle Physics
Data Grid: www.ppdg.net/
Pastry: www.research.microsoft.com/~antr/pastry/
Tapestry: www.cs.berkeley.edu/~ravenben/tapestry/
The Authors
DAVID P. ANDERSON and JOHN KUBIATOWICZ are both associated with the
University of California, Berkeley. Anderson was on the faculty of the
computer science department from 1985 to 1991. He is now director of the
SETI@home project and chief science officer of United Devices, a provider
of distributed computing software that is allied with the distributed.net
project. Kubiatowicz is an assistant professor of computer science at
Berkeley and is chief architect of OceanStore, a distributed storage
system under development with many of the properties required for an
ISOS.
